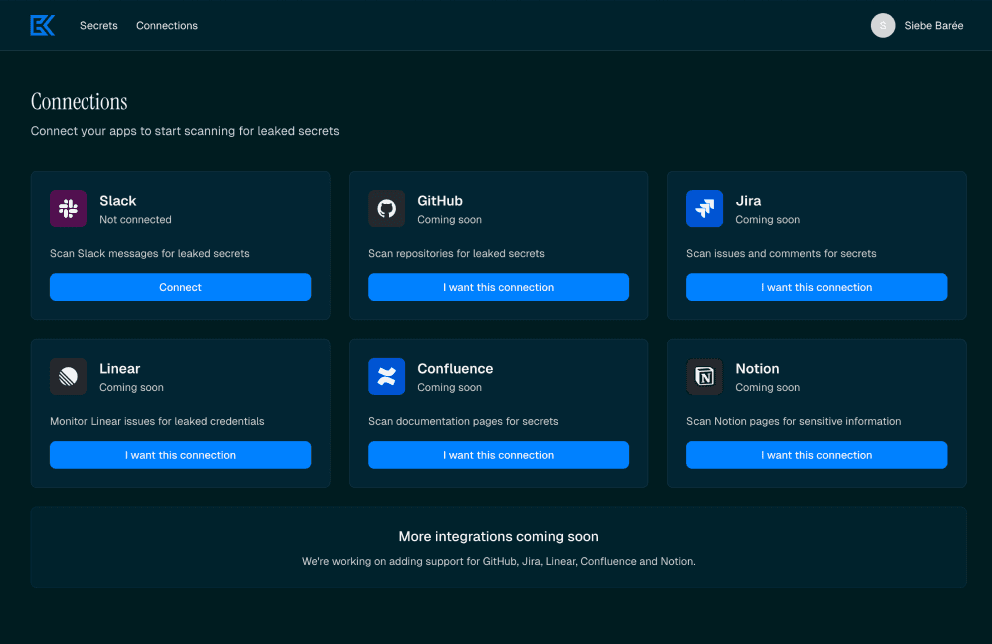
Confidence from the first scan
Enkryptify helps teams find exposed secrets, centralize them in a secure vault and keep access auditable across environments.
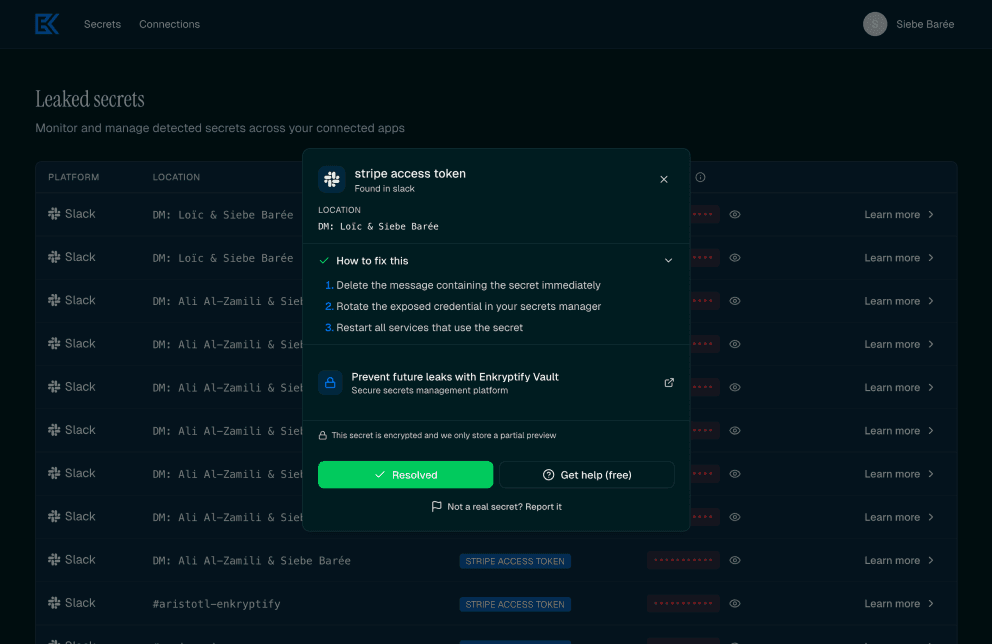
Most teams don't know they're vulnerable until it's too late.
39M
secrets exposed on GitHub in 2024
70%
of secrets detected in 2022 remain active today
2.4%
of Slack channels contain secrets
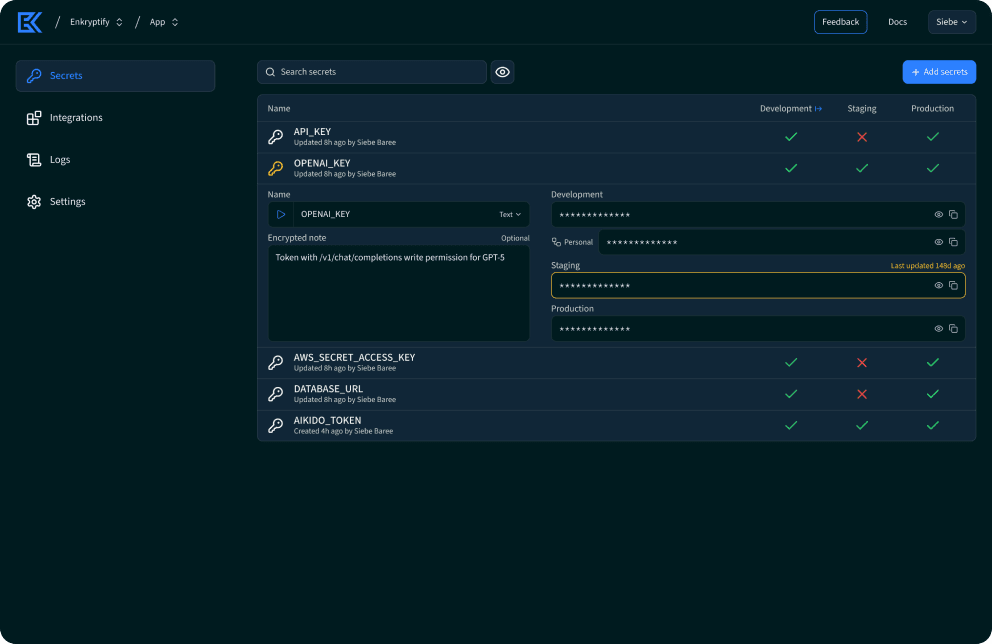
From discovery to deployment
Complete secrets lifecycle management. Find leaks, store securely and manage access across your entire stack.
01
—
Discover
Scan collaboration tools and repos to spot exposed secrets and weak practices early.
02
—
Store
Centralize secrets in an encrypted vault with least-privilege access and full audit trails.
03
—
Automate
Rotate credentials and enforce policies automatically as your stack scales.
04
—
Remediate
Replace leaked or overused secrets fast and verify fixes across every environment.